É isso aí pessoal! Foi anunciado o lançamento do FreeBSD 11. O anúncio na íntegra está logo abaixo:
FreeBSD 11.0-RELEASE Announcement
The FreeBSD Release Engineering Team is pleased to announce the
availability of FreeBSD 11.0-RELEASE. This is the first release of the
stable/11 branch.
Some of the highlights:
* OpenSSH DSA key generation has been disabled by default. It is
important to update OpenSSH keys prior to upgrading. Additionally,
Protocol 1 support has been removed.
* OpenSSH has been updated to 7.2p2.
* Wireless support for 802.11n has been added.
* By default, the ifconfig(8) utility will set the default regulatory
domain to FCC on wireless interfaces. As a result, newly created
wireless interfaces with default settings will have less chance to
violate country-specific regulations.
* The svnlite(1) utility has been updated to version 1.9.4.
* The libblacklist(3) library and applications have been ported from
the NetBSD Project.
* Support for the AArch64 (arm64) architecture has been added.
* Native graphics support has been added to the bhyve(8) hypervisor.
* Broader wireless network driver support has been added.
For a complete list of new features and known problems, please see the
online release notes and errata list, available at:
* https://www.FreeBSD.org/releases/11.0R/relnotes.html
* https://www.FreeBSD.org/releases/11.0R/errata.html
For more information about FreeBSD release engineering activities, please
see:
* https://www.FreeBSD.org/releng/
Important Notes
Please note, as a result of the timing between the withdrawn
FreeBSD 11.0-RELEASE images being available before the official
announcement and several last-minute issues being discovered, uname(1)
will display FreeBSD 11.0-RELEASE-p1, as the images were generated from a
patch-level revision of the releng/11.0 branch.
Users that have installed FreeBSD 11.0-RELEASE from the images originally
available on the mirrors or from freebsd-update(8) prior to the rebuild
of the final release are urged to upgrade their systems to
FreeBSD 11.0-RELEASE-p1 immediately.
Users upgrading from system source code should use releng/11.0 revision
r306420.
Users upgrading from freebsd-update(8) should follow these instructions
to update their systems to FreeBSD 11.0-RELEASE-p1:
Upgrading from FreeBSD 11.0-RELEASE
# : > /usr/bin/bspatch
# freebsd-update fetch
# freebsd-update install
Upgrading from FreeBSD 10.3-RELEASE and Earlier
# : > /usr/bin/bspatch
# freebsd-update upgrade -r 11.0-RELEASE
# freebsd-update install
<reboot the system>
# freebsd-update install
<rebuild third-party software>
# freebsd-update install
EC2(TM) users are urged to read the Errata Notes for FreeBSD 11.0-RELEASE
regarding an issue discovered very late in the release cycle that may
cause the system to hang during the boot process when upgrading from
previous FreeBSD versions. New EC2(TM) installations are not affected,
but existing installations running earlier releases are advised to wait
until the issue is resolved in an Errata Notice before upgrading.
Dedication
The FreeBSD Project dedicates the FreeBSD 11.0-RELEASE to the memory of
several members of the community:
* Stefan Farfeleder
* Juergen Lock
* Ben Perrault
* Paul Schenkeveld
* Volker Werth
May they rest in peace.
Availability
FreeBSD 11.0-RELEASE is now available for the amd64, i386, powerpc,
powerpc64, sparc64, armv6, and aarch64 architectures.
FreeBSD 11.0-RELEASE can be installed from bootable ISO images or over
the network. Some architectures also support installing from a USB memory
stick. The required files can be downloaded via FTP as described in the
section below. While some of the smaller FTP mirrors may not carry all
architectures, they will all generally contain the more common ones such
as amd64 and i386.
SHA512 and SHA256 hashes for the release ISO, memory stick, and SD card
images are included at the bottom of this message.
PGP-signed checksums for the release images are also available at:
* https://www.FreeBSD.org/releases/11.0R/signatures.html
A PGP-signed version of this announcement is available at:
* https://www.FreeBSD.org/releases/11.0R/announce.asc
The purpose of the images provided as part of the release are as follows:
dvd1
This contains everything necessary to install the base FreeBSD
operating system, the documentation, and a small set of pre-built
packages aimed at getting a graphical workstation up and running.
It also supports booting into a "livefs" based rescue mode. This
should be all you need if you can burn and use DVD-sized media.
disc1
This contains the base FreeBSD operating system. It also supports
booting into a "livefs" based rescue mode. There are no pre-built
packages.
bootonly
This supports booting a machine using the CDROM drive but does
not contain the installation distribution sets for installing
FreeBSD from the CD itself. You would need to perform a network
based install (e.g., from an FTP server) after booting from the
CD.
memstick
This can be written to an USB memory stick (flash drive) and used
to do an install on machines capable of booting off USB drives.
It also supports booting into a "livefs" based rescue mode. There
are no pre-built packages.
As one example of how to use the memstick image, assuming the USB
drive appears as /dev/da0 on your machine something like this
should work:
# dd if=FreeBSD-11.0-RELEASE-amd64-memstick.img \
of=/dev/da0 bs=1m conv=sync
Be careful to make sure you get the target (of=) correct.
mini-memstick
This can be written to an USB memory stick (flash drive) and used
to boot a machine, but does not contain the installation
distribution sets on the medium itself, similar to the bootonly
image. It also supports booting into a "livefs" based rescue
mode. There are no pre-built packages.
As one example of how to use the mini-memstick image, assuming
the USB drive appears as /dev/da0 on your machine something like
this should work:
# dd if=FreeBSD-11.0-RELEASE-amd64-mini-memstick.img \
of=/dev/da0 bs=1m conv=sync
Be careful to make sure you get the target (of=) correct.
FreeBSD/arm SD card images
These can be written to an SD card and used to boot the supported
arm system. The SD card image contains the full FreeBSD
installation, and can be installed onto SD cards as small as
512Mb.
For convenience for those without console access to the system, a
freebsd user with a password of freebsd is available by default
for ssh(1) access. Additionally, the root user password is set to
root, which it is strongly recommended to change the password for
both users after gaining access to the system.
To write the FreeBSD/arm image to an SD card, use the dd(1)
utility, replacing KERNEL with the appropriate kernel
configuration name for the system.
# dd if=FreeBSD-11.0-RELEASE-arm-armv6-KERNEL.img \
of=/dev/da0 bs=1m conv=sync
Be careful to make sure you get the target (of=) correct.
FreeBSD 11.0-RELEASE can also be purchased on CD-ROM or DVD from several
vendors. One of the vendors that will be offering FreeBSD 11.0-based
products is:
* FreeBSD Mall, Inc. https://www.freebsdmall.com
Pre-installed virtual machine images are also available for the amd64
(x86_64), i386 (x86_32), and AArch64 (arm64) architectures in QCOW2, VHD,
and VMDK disk image formats, as well as raw (unformatted) images.
FreeBSD 11.0-RELEASE amd64 is also available on these cloud hosting
platforms:
* Amazon(R) EC2(TM):
AMIs are available in the following regions:
us-east-1 region: ami-6ceaab7b
us-west-1 region: ami-a3f9b7c3
us-west-2 region: ami-6926f809
sa-east-1 region: ami-a1ff6dcd
eu-west-1 region: ami-36581e45
eu-central-1 region: ami-2352ae4c
ap-northeast-1 region: ami-a236e9c3
ap-northeast-2 region: ami-a49044ca
ap-southeast-1 region: ami-c39337a0
ap-southeast-2 region: ami-5920133a
ap-south-1 region: ami-7c3a4e13
AMIs are also available in the Amazon(R) Marketplace at:
https://aws.amazon.com/marketplace/pp/B01LWSWRED/
* Google(R) Compute Engine(TM):
Instances can be deployed using the gcloud utility:
% gcloud compute instances create INSTANCE \
--image freebsd-11-0-release-p1-amd64 \
--image-project=freebsd-org-cloud-dev
% gcloud compute ssh INSTANCE
Replace INSTANCE with the name of the Google Compute Engine instance.
* Hashicorp/Atlas(R) Vagrant(TM):
Instances can be deployed using the vagrant utility:
% vagrant init freebsd/FreeBSD-11.0-RELEASE-p1
% vagrant up
FTP
FreeBSD 11.0-RELEASE may be downloaded via ftp from the following site:
* ftp://ftp.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/11.0/
However before trying this site, please check your regional mirror(s)
first by going to:
* ftp://ftp.<your_country_code>.FreeBSD.org/pub/FreeBSD
Any additional mirror sites will be labeled ftp2, ftp3 and so on.
More information about FreeBSD mirror sites can be found at:
* https://www.FreeBSD.org/doc/en_US.ISO8859-1/books/handbook/mirrors-ftp.html
FreeBSD 11.0-RELEASE virtual machine images may be downloaded via ftp
from:
* ftp://ftp.freebsd.org/pub/FreeBSD/releases/VM-IMAGES/11.0-RELEASE/
For instructions on installing FreeBSD or updating an existing machine to
11.0-RELEASE please see:
* https://www.FreeBSD.org/releases/11.0R/installation.html
Support
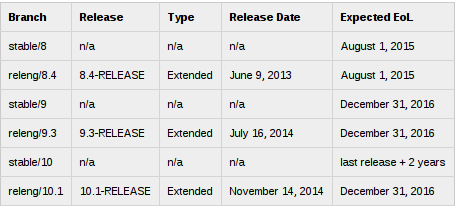
Based on the new FreeBSD support model, the FreeBSD 11 release series
will be supported until at least September 30, 2021. The first point
release, FreeBSD 11.0-RELEASE, will be supported until at least three
months after FreeBSD 11.1-RELEASE. Additional support information can be
found at:
* https://www.FreeBSD.org/security/
Acknowledgments
Many companies donated equipment, network access, or man-hours to support
the release engineering activities for FreeBSD 11.0 including The
FreeBSD Foundation, Yahoo!, NetApp, Internet Systems Consortium, ByteMark
Hosting, Sentex Communications, New York Internet, Juniper Networks,
NLNet Labs, iXsystems, and Yandex.
The release engineering team for 11.0-RELEASE includes:
Glen Barber <gjb@FreeBSD.org> Release Engineering Lead,
11.0-RELEASE Release Engineer
Konstantin Belousov <kib@FreeBSD.org> Release Engineering
Bryan Drewery <bdrewery@FreeBSD.org> Release Engineering, Package
Building
Marc Fonvieille <blackend@FreeBSD.org> Release Engineering, Documentation
Rodney Grimes <rgrimes@FreeBSD.org> Release Engineering Emeritus
Xin Li <delphij@FreeBSD.org> Release Engineering, Security
Officer
Remko Lodder <remko@FreeBSD.org> Security Team Liaison
Hiroki Sato <hrs@FreeBSD.org> Release Engineering, Documentation
Gleb Smirnoff <glebius@FreeBSD.org> Release Engineering, Security
Officer Deputy
Marius Strobl <marius@FreeBSD.org> Release Engineering Deputy Lead
Robert Watson <rwatson@FreeBSD.org> Release Engineering
Special thanks to Colin Percival <cperciva@FreeBSD.org> for his
assistance regenerating the freebsd-update(8) builds for the final
release.
Trademark
FreeBSD is a registered trademark of The FreeBSD Foundation.
ISO Image Checksums
amd64 (x86_64):
SHA512 (FreeBSD-11.0-RELEASE-amd64-bootonly.iso) = 9ba85ec5e36d0b7d57a0a8d2bc3624c39a8c453f3009d049c207a80879d5ddc337646b09f9ed1badebe18afc5e0285d4133b659f4bccfc84d1996f8ba960c90b
SHA512 (FreeBSD-11.0-RELEASE-amd64-bootonly.iso.xz) = c01dbc9272b81af59bcbef534b1baccd3cbc47dbfed8525384e358df214fcb885f66832c6614f5bb4d119bbdceba66a835d4393ecbcd97ae4fd008efbdcb1c69
SHA512 (FreeBSD-11.0-RELEASE-amd64-disc1.iso) = a9ab27f18a53130ee25dea975059ceab7307deafb991839e228ab3a45346c0b8060766d183985ae28716931f211ad2b22fc13c819516a4e8ab63aa6162133c4d
SHA512 (FreeBSD-11.0-RELEASE-amd64-disc1.iso.xz) = c572439d8431bd3def669bf4e304fa06ca9ee6dda4bfa31755220dc879e15e0508f7b8e56fa4c0a664c848864c3b52d7e0e285b2a6529a386915b03b371f86b2
SHA512 (FreeBSD-11.0-RELEASE-amd64-dvd1.iso) = 0021c15ec1b3a15666cd0cb20f4d8855cf629136085f3454c797a0240c0818878f2e16ca0cba4c8567150ba95843360fb50fd92b0c459851fdff06e1bc43d5e8
SHA512 (FreeBSD-11.0-RELEASE-amd64-dvd1.iso.xz) = 63dda54a43ea5b54f0574a9a3092623f1f9ffa8b66ccea5508ed3a4dd073d4a5c81423f1663df39986fa8289716cf37fb1ba2767fd91a9fd425de6c2024e6fd4
SHA512 (FreeBSD-11.0-RELEASE-amd64-memstick.img) = 65ae116ffd12decb937634dc40a23088f5ebd51aabce02d663ad6488e0a4c8c8587c7b53aea07a51c3e458880c1882b9fc7cf9996c87f6af8cf85efe4d111ddd
SHA512 (FreeBSD-11.0-RELEASE-amd64-memstick.img.xz) = 4cf01fc51d9f89bc581262525ebb30299443c3b86b309cc8230b6eed778afcb4776a6d602dcf85b2bbe1fde824c2cda8cbeed8ab57bb03103e369ca73880525b
SHA512 (FreeBSD-11.0-RELEASE-amd64-mini-memstick.img) = 89759449f9ad0fd8d2e770132fba225fccc59e954417a5046ae82a264dd15127a9ce7ab7391ec5f6cc589ff051b3a5a5b1ec9389fa5b6a1b34040ecc41e74197
SHA512 (FreeBSD-11.0-RELEASE-amd64-mini-memstick.img.xz) = 7b919047f7d4d25e2e0fe979f41f43a3fb153016044deec0b17c56402c18958db6ec80bc9638acae281ea7eb80498a8fdbee85e522bed5e30e9c5abfd2c257dc
SHA256 (FreeBSD-11.0-RELEASE-amd64-bootonly.iso) = f373dbdb9ce80c4f1b4a50d565356a1172d42ad00cf2c4cbe3131d0b566db5b4
SHA256 (FreeBSD-11.0-RELEASE-amd64-bootonly.iso.xz) = 49dcf35eabae9f63660f29f302f3854e05d4cdc046e4cfcef91abf23631c64d6
SHA256 (FreeBSD-11.0-RELEASE-amd64-disc1.iso) = 08b12f2dc378f7a61b5469219824c74a2f9faef580acc85ffab45365df79872d
SHA256 (FreeBSD-11.0-RELEASE-amd64-disc1.iso.xz) = 9177103547e77f018c1fc8a8bfc621eac7d329caaf778a2386bd197c0c02385e
SHA256 (FreeBSD-11.0-RELEASE-amd64-dvd1.iso) = 5f03fd91c1b604579e2830b33da16f1c7e586f5274e36e0e26e4f4ff497d63e8
SHA256 (FreeBSD-11.0-RELEASE-amd64-dvd1.iso.xz) = 20652e206f4b249e926330801f78139de7f9444921d91ded75665441a293631c
SHA256 (FreeBSD-11.0-RELEASE-amd64-memstick.img) = 04cdc9575d674a821b4a099743545b35e5f57ce274872297c5f251d25322f299
SHA256 (FreeBSD-11.0-RELEASE-amd64-memstick.img.xz) = ef4f820eaa8cd1911a4c9b1ededa0016184a4154e98d048aad3c71f6e45e8fbe
SHA256 (FreeBSD-11.0-RELEASE-amd64-mini-memstick.img) = 18a3f566a94fa3167ac6af9f0a65f391c101fafe74d44a3db70f6b8ed35ab69a
SHA256 (FreeBSD-11.0-RELEASE-amd64-mini-memstick.img.xz) = 944b2f54cb59186904664c18fea7950eb3780fad440d7fd383377b5b5c7c6f48
i386 (x86):
SHA512 (FreeBSD-11.0-RELEASE-i386-bootonly.iso) = f7131f017035617181da8ebcee35c841c51c73f0520562a55e15a8fa8db21d56b1b0aaff9c9fc08e5524abd8b09d3740994a73f54d07dfe6b0406102a83cb146
SHA512 (FreeBSD-11.0-RELEASE-i386-bootonly.iso.xz) = c3b1f491c41b6452d2664da7c861dc05bdfd7a3493079ac23e5e818e1ea650e06ec6c372cbcbd94d06237dfe90f80845e09804ca310d5a9b18c0425863829f13
SHA512 (FreeBSD-11.0-RELEASE-i386-disc1.iso) = f875c196bd273461b7a80c9cfed465fd1d60379a6c950498bf9099014e1e0f2ad94e6e28856a4d6a04635a28e88286799539f4f1d1bb6127ae96ec58250500ca
SHA512 (FreeBSD-11.0-RELEASE-i386-disc1.iso.xz) = 319b325e3c93d628285c256747be6b559a4251a18fd2b8e4819d619372557dfec664fa6b123ef9226532ef34acbada8234af7eef7237ed6e89422699e67c095c
SHA512 (FreeBSD-11.0-RELEASE-i386-dvd1.iso) = 9245d50d2d79ee24eaccc19cb93d66b71fe0efe37f80cbfb2d545c3496e365658a0e0832a0ef5911479b854b1a742e6f81862775e1e3f51ceb0a73c0adbed568
SHA512 (FreeBSD-11.0-RELEASE-i386-dvd1.iso.xz) = 3920065fd2b97ae7875ab7ac9ad2f83729884cba81ee04636f1b4d08317de8f542a22a9804d92121d932c95965d3c02fd957f23d4ce8b02aac053a44c9f8d1ed
SHA512 (FreeBSD-11.0-RELEASE-i386-memstick.img) = edd0008f4efce1fea93b2401fbfba116a00999ac047cd904a392c5c0fde60b224dbfb89eb6a0a8848372cf0f7936ed2d153620def7bb0811d28d84109bfbb7c7
SHA512 (FreeBSD-11.0-RELEASE-i386-memstick.img.xz) = 6ed053e13e912c40f97dafd5dafced4bbfa724fcfdf8507462217b875a3e041f21e84d2d7b46d73fc57d928380fd8625fa88d1f5aeab2208867735b264d6e43f
SHA512 (FreeBSD-11.0-RELEASE-i386-mini-memstick.img) = e716caedc857352efa6b7186b7d030eac52c6c2e7cd9f12bee3c53f0b6b2842f206ef800b4ec838449f5e6ecf76dc1b79a4bcb5b4bf003163c08c9e5c0abe734
SHA512 (FreeBSD-11.0-RELEASE-i386-mini-memstick.img.xz) = 02253768ad9b328adb45b2604a526f275d110ace6c01308ab2294caa1dfd510fe44841fd882750f787b4bab66bea3b40af41e60b14646716956475b20dd37f73
SHA256 (FreeBSD-11.0-RELEASE-i386-bootonly.iso) = 725730204e5ee80e23a8d6844f32434f3f7a95b4a6142a5e2b634f6e20d1b5a6
SHA256 (FreeBSD-11.0-RELEASE-i386-bootonly.iso.xz) = 1fb3bba1cc2a3620c354d997d03e2a5b13e353ef162fb7edb6a08135b3f79b0b
SHA256 (FreeBSD-11.0-RELEASE-i386-disc1.iso) = 6638ed4cce829cf0f8c120962140e4c24587f0a0ebe0567661f95cbfb2ebee78
SHA256 (FreeBSD-11.0-RELEASE-i386-disc1.iso.xz) = 589b60d44223cee01b907a9e319aa399baf7e558fe714b580c70eda2e5ddca66
SHA256 (FreeBSD-11.0-RELEASE-i386-dvd1.iso) = 2eef5e53fd5600b160b4810bb9e81c81a38e6742817a2b3bd455d6b327bf1ffd
SHA256 (FreeBSD-11.0-RELEASE-i386-dvd1.iso.xz) = 610e38ec6157fded7d6af086944d9289c00a806c4bd2e18135a74251e832e1e4
SHA256 (FreeBSD-11.0-RELEASE-i386-memstick.img) = ea58615a2a018dacc9331cc0dd202a1395b144e0dbf59422a154eaf0d4fa82a8
SHA256 (FreeBSD-11.0-RELEASE-i386-memstick.img.xz) = e17719d4c88c39704a5a314c24155773792c7b79ce4955c51925175ebf7e85c9
SHA256 (FreeBSD-11.0-RELEASE-i386-mini-memstick.img) = 25002217812b7eb44979b7a1dc115344de14ae641d899a47c60a2833648607f8
SHA256 (FreeBSD-11.0-RELEASE-i386-mini-memstick.img.xz) = 1a93f1c47ed5ef783df3b520048902ca16f34645f85faf2b433d63b914ad2a55
powerpc:
SHA512 (FreeBSD-11.0-RELEASE-powerpc-bootonly.iso) = 88da48dd6d6e21430a6868e4a44c30f26fe252c21199da3b2806dd7ce816a30159ca3294c56c59725c0e95c56142ee74c736a2c006d1f306a3572e0f9c235d9b
SHA512 (FreeBSD-11.0-RELEASE-powerpc-bootonly.iso.xz) = 1c852493429dd4377af5eec4bd3c6ba3ae0996d8de4fb50739ce601cc545f3fae47b712a50ca7e5868c1d26b5b02f4a5691e2a0ac01fd18a06336472bdfb6a16
SHA512 (FreeBSD-11.0-RELEASE-powerpc-disc1.iso) = f371b584e41ecfbb62c0e96c12996e99c8e238f0126f01bc059b5458c3c18ea26ae03ce8c84f412203a3e2868bc4f74b060796507ea823d905eb041fd82a3ab1
SHA512 (FreeBSD-11.0-RELEASE-powerpc-disc1.iso.xz) = d675c4c3b777d453f15427c131b9b26ca14a6f2b70665ce0411d13c29e23d951f5cb3c021636869db3ba7ea377083c0c7b081122b5621660fee4243f564756ce
SHA512 (FreeBSD-11.0-RELEASE-powerpc-memstick.img) = ca77d858f15510bd121e0f18cd8bcdba44e0eea3d0d17026529ffcd19c760f5fd52ebe7e04dbc0b159e21082df81b6610a950d217c84d0cf47f872c50501719b
SHA512 (FreeBSD-11.0-RELEASE-powerpc-memstick.img.xz) = 308464d636efc897a85fc6c1705700d9cc4ceb713b9a5af5b14c8fb661ea54bd1de44a8cb3ba65ccf8db62fc2f27a7443f415812343fff6163f1449eb7fa9dcc
SHA512 (FreeBSD-11.0-RELEASE-powerpc-mini-memstick.img) = 223acd473c6389e8529c031574a57f292f1e62b6a7d43ba87e02ba4d7d02b0f10ab4fd2e6a554271f3fe0e1aeb3f655014e74bb4f775f473f9d6b58e33ade130
SHA512 (FreeBSD-11.0-RELEASE-powerpc-mini-memstick.img.xz) = a4fb3b5ad43b06a2ea13eb71c06a34e3b58b2086ea526017396cf88640b648a88db5a40e11c552f5ac7d8ec649e12b0df19c096d3a9a6943fde8d67aeb3a9fea
SHA256 (FreeBSD-11.0-RELEASE-powerpc-bootonly.iso) = 13415ab9fe6052a54db59e053554b3931234c91c8c59a12d4e51a27299754aaf
SHA256 (FreeBSD-11.0-RELEASE-powerpc-bootonly.iso.xz) = 5c25cb6ac77915ee4a0ed078c78fbed840e7fc75f2e69db51f54c5ff6b122cd4
SHA256 (FreeBSD-11.0-RELEASE-powerpc-disc1.iso) = efaccbe7018541225989ff6befb2082ce3409f5a7669f19ac0d3d003c869436e
SHA256 (FreeBSD-11.0-RELEASE-powerpc-disc1.iso.xz) = b12b87fec19986047911c47143da50bb37be765ca3842711872d1cca7785db2a
SHA256 (FreeBSD-11.0-RELEASE-powerpc-memstick.img) = cd5a5a7492076cd484cad14ab327307769592a21592de83c1b7946dd8ed82811
SHA256 (FreeBSD-11.0-RELEASE-powerpc-memstick.img.xz) = c3cd1819c993a706c0657a6b8f78de8602211a5d287bfef9cca1d4c90b11e93e
SHA256 (FreeBSD-11.0-RELEASE-powerpc-mini-memstick.img) = 21cdefe0d0f895229df97891657fb3c4118e51e24b4b7fe9b75d5da3e61546a5
SHA256 (FreeBSD-11.0-RELEASE-powerpc-mini-memstick.img.xz) = e7e790e5e58d1a4f1462faf4fc1f26e742e843e3ccfc2e856d274caad4775e54
powerpc64:
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-bootonly.iso) = 728a08c16abc6eeabc27169132964e9f146e065a89050de77420d0ec9b6cc35c8c54dfb30b55ec47be29863e4901a461378628814a84f8aaa117d20ee412b744
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-bootonly.iso.xz) = defb1520fdae02eaa88ddcb12858100c88d09cca48a207ec75b6cbf185bbcf09991202ec9aead0618311864af528ca28e88826fb16361254936de6bbcf6f66a8
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-disc1.iso) = d24783d884a1829667268c0ca8a567cc1fa363e4edea11ead59c618fdf520acc5dd7ff5bfe9cdb482ff7dc6c49ad9ae446061894b008db6ed74e61da7232a56d
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-disc1.iso.xz) = b7caf299570ee5c76ec9098c5f6d589e905c2d24c510164be25d294454cdfc7c5412e3d7d0cc5e08b43021a2d858664e8110f7c2481701d951653602a93d314f
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-memstick.img) = 895947ead25b08ece22bbcab9ebed6d0997be53f312b92788e207fa9daa6472d51b165f0a5d2bfa8bcd0504b70f5ca86b9e6a0c821c487e237aa8ad466fa3424
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-memstick.img.xz) = 23321419ef5995932784d848a45fd9096cab3038e21ab592b5180b5bf2a248118a4fdad0760ddf40eddb7ee55874c41c0fcb6cebeb6e270948248b871016ec9c
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-mini-memstick.img) = 1f7d199f38d2cf58f3e38a4f943c3fd5779ab4c847856a3ea96d5d93d6fc2d636cd0c1dd85ffa209dc38f455c39e40679dcc7eb7b0a3c4098963408d9ba41f9c
SHA512 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-mini-memstick.img.xz) = 166eaddbe1ba4dece384d3ef7a7b60b33301b7820e92ce6636195b2c4e7208b45192c9aaf5d29416fece0c9df169fbf4e342fd0c84b8fc54c0683f8ecb2a44e9
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-bootonly.iso) = 6b0f9166843fd8440a31cf0e9823cee212e8a2ac25a0929ff3963f639cba7850
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-bootonly.iso.xz) = a0448ac93b6764b5f94580f9055038a7111f60900956faa689a71c2690896829
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-disc1.iso) = 04f5735215adba151ed0d78c86bec287fbd155e539bc7ae614eee180ac9d9520
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-disc1.iso.xz) = a311c943bc84fd022c06296a77eeb537bd19a0ec2be0c43de425b7f5e5b7ee9d
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-memstick.img) = 42d03a02fb0dc45baf7de9a7902e80c3de1cb4e64ccb11b9b954a7245d38ec2b
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-memstick.img.xz) = a01e7e590f215bfbf89c8a99396c456b61189c4f0e1e174286ea2966cd1f8fcb
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-mini-memstick.img) = 3839c94be58b56b021f760a6ef31c555b034e4ac436ad9d1d17e838ce6984e62
SHA256 (FreeBSD-11.0-RELEASE-powerpc-powerpc64-mini-memstick.img.xz) = 58cdf3be35ed8e8fbcc620bda28e808077707396494a550fe63b3d7add6ae72e
sparc64:
SHA512 (FreeBSD-11.0-RELEASE-sparc64-bootonly.iso) = 7b724a9b0831a181658465287daec4bcb3de7302bf5778eafd3a023e18d16abe10e0279af9f3e2cb6b5b1687dfe4963dd5d7886278801ebd93c56c72b6c8529a
SHA512 (FreeBSD-11.0-RELEASE-sparc64-bootonly.iso.xz) = 6fdbe0cae1be741038d14ef751c9057082bcefa0de4dedbb1cf2c1b7507ac0348a67b6bb269330bbefc3b89a858c7c30cbd1f4f9e1010b17fae21af711530585
SHA512 (FreeBSD-11.0-RELEASE-sparc64-disc1.iso) = 375ffa9a412b9077cacce3aa9526fb501e97e9cbb009298fefcef6ccee58c5b25fb5b3e50bc89a9838d44fbbf8ded4b0185d19712330c721ce551fad94033c87
SHA512 (FreeBSD-11.0-RELEASE-sparc64-disc1.iso.xz) = 48731490a5463bf468f4ba2f5450ef9603dd1939d3f92bee020c36e8a9fca191b780768b8899776550529e70b4b1d3f25906ce88aba9f83f7a348c8662edd912
SHA256 (FreeBSD-11.0-RELEASE-sparc64-bootonly.iso) = 27a5155e38dba88a3630086b69f366be3b8fab2a93f569e583a987aa4915889d
SHA256 (FreeBSD-11.0-RELEASE-sparc64-bootonly.iso.xz) = 6503bfe2988d6451f8106061e9437da11817263d3cc821f44ad9caa3d7be84b8
SHA256 (FreeBSD-11.0-RELEASE-sparc64-disc1.iso) = 5d34d672df0f5a1338e0c1108cbf31ff7a0dd86e81db35559d40133990d31a0d
SHA256 (FreeBSD-11.0-RELEASE-sparc64-disc1.iso.xz) = ea075075fd7733ec3e1839251b498148a0192661e63e7a293f98a7add6f48bf7
aarch64:
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64-memstick.img) = 218efc6c2ec6d27dd6825b4bdf4f67acb6cde98268f2ab9e711f7b095920a9f1968d5bea7b46590e8ad60673b6d8dded21654b204d6a44d50c4830accbd418ba
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64-memstick.img.xz) = 4ba8ce52422ac8cc77e83eaf28aaa745d8f119134ead06f19f66d76b09c7360597c74b45b787a6bb3dc276877ee44a8fc031a28720f5f79dcccb3de26a303cae
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64-mini-memstick.img) = acd48a274fae57733c79899f7037454c5e308d198ac97ad76c9efdac64c78f72156dadb3ad2a996ca6d04e49f6aaba2c177326c5dadbdd0ba8e3a3ba53dc88ed
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64-mini-memstick.img.xz) = aec61d00e41286c3ea5016c93f44ef971c2584e8725f0563203e7d56df976c96332ce9265721e87d1a092c64477171f779d00aca5752fe8026a2d06f5b540a74
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64-memstick.img) = 63995c9edcb34006bd428e32506374ea07c763cffc4b0575821042f9b99dae07
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64-memstick.img.xz) = 823f61d65ee65bb23d1d57b5595cb20e19a5b39b59e27a459e27e776d2a69b04
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64-mini-memstick.img) = 1ffbaba4763276e938b95ef7b494ec5eeefb99f84a62b0f60b80fe78fcb4d4eb
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64-mini-memstick.img.xz) = b29508ce2a83c53972936b2a74146f195d456aa9567899baaac8374347a23f33
armv6 BANANAPI:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-BANANAPI.img.xz) = fc48ffa948608bb68429e424571d02c729166e3da5466b9db40807d1f73f66be993a68bd186c46f6539d69b2ab53aae6414b4e6ff6a900289bdef51b0cf9b151
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-BANANAPI.img.xz) = ae25860ffbe34c72ff2823708c90ce154378574d28060f7b6ad8cd935e1c41d0
armv6 BEAGLEBONE:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-BEAGLEBONE.img.xz) = 7df332447c0d9712dc31f6ccd763f8d2ae2295ccc49c074ca7aab4b317500cd16074fd8a406b5a3ece68a21221d548b13868bbf1ce2baf69b526200f0bf70a5e
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-BEAGLEBONE.img.xz) = 401edf4dd62d8274e6e9b38bdb5b9de193bf7b5e69b22398be54768175e8315e
armv6 CUBIEBOARD:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-CUBIEBOARD.img.xz) = a2ff7c46207a273eba20309999417b3863ae52513ad7fe43dae0b180eccd5df7b761eb25ddb49eaa7a7ec13444b9ef596ce088d657a4f6ffe2bb787630197d6d
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-CUBIEBOARD.img.xz) = d3aaae1e4f3e7ee81b41784fb83099d8ad3d7f668ad0a6b93ca566d742f7a308
armv6 CUBIEBOARD2:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-CUBIEBOARD2.img.xz) = fbff0b9dac00e95857ee0a5d748ad015435dfbc1f9d57a464317c177d03969d08c14856fa77ca0f2de69a98c26657731a87e58c7408a010732bb5016efecc19c
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-CUBIEBOARD2.img.xz) = bc42a99cf8c0eb18f84da48b79b4601ceea6084cf03ae259542365077fa6b4d3
armv6 CUBOX-HUMMINGBOARD:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-CUBOX-HUMMINGBOARD.img.xz) = 17d412877bc6c41360683dc91698c1044487b733de8071f6610fe47546f193e4355fc08b17a8ee9d90b0ffad282d1a7e372622214694f1e09d20b05181210854
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-CUBOX-HUMMINGBOARD.img.xz) = 36c250720969641ba98d903ff1bafb807b68d5a80cb56040d1a6c7deec2eb52d
armv6 GUMSTIX:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-GUMSTIX.img.xz) = e6fc884f64931dfa60d86295222c3d41d0da0e764b27f6ca9281c593766a4545520e3297dfe98da5b6cd63632c79f0ecf4252386bfc705c883f9f43ef6b5f700
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-GUMSTIX.img.xz) = c027923ad679f174903b05c45e6f185a7df98f17029dc866dc0cd78dc870031e
armv6 RPI-B:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-RPI-B.img.xz) = 6074d9486efbe06b81ea9f9a6573d321fbd25d1d4485c1385a14d1a91b188679dc4830b599bd29c418403a5ae948fe5cafa82fa2157c38555eeef08fa9eab2a9
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-RPI-B.img.xz) = a417f112f42c7609a07bcf4437a3480bf186ae517f66c0ca3cb2e90533c14e8d
armv6 RPI2:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-RPI2.img.xz) = f6fc7dd3077e4941190395b694b34db492da97dc074adcab99c8cbcf71b6be499e9deb739c2f5fa6639d978508ffd7a995e4516899b55cc0d577b7f8e0f99f1f
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-RPI2.img.xz) = cb7f3f143bb04428c4d7dff106a90d51c162668d44fdb85fdb18440fa679d4ed
armv6 PANDABOARD:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-PANDABOARD.img.xz) = 0d2e4c6f954055872ed9eb6e7253b0192b985728112de1a10e80528c5988fd6c6791ba6d0ce18ceaffd10bdf32347e34f41b46220aac59bd1587b65170da34d9
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-PANDABOARD.img.xz) = dd0af02516f842548b27001b85e3fe6dbd4091b8c2dac2e468abc8e3e714b8bd
armv6 WANDBOARD:
SHA512 (FreeBSD-11.0-RELEASE-arm-armv6-WANDBOARD.img.xz) = b3be509f69ae5adf50e0804bd5380e8f8286ad50c933314f3ab92974d05184813f9f1e6998bc3b8f85c091dd960f73f48ce0e71546355d60db52f2d31509274f
SHA256 (FreeBSD-11.0-RELEASE-arm-armv6-WANDBOARD.img.xz) = 301e58b1b250b97f455b5f9e75930da919eebf0ad71f522cd8f1024a2e122316
Virtual Machine Disk Image Checksums
amd64 (x86_64):
SHA512 (FreeBSD-11.0-RELEASE-amd64.qcow2.xz) = 598a0d2460ed4c059f162a285e0c21892615d2916c5d1899a26859bc5fa74593a63e20cbdceb439ef72c6c65d6c3bc0d676e5da9a6cecac21c2771ba9e0b7915
SHA512 (FreeBSD-11.0-RELEASE-amd64.raw.xz) = 1bfdef9a106e41134cf92c5ceb7f7da468293d6611d16c0bc51482a8fb3088064204bacfe6a8b1afda169d9ab63e4bbd1c9ba1de06fe3fd604864d3fb0c07326
SHA512 (FreeBSD-11.0-RELEASE-amd64.vhd.xz) = 9f6cd27d91882e00edda7f9153814c036b4cff666f73dfac6d5b31b0491b942095d972fe5d8abf338791af66a837321a53cacbf091c43b1ee625b9f58e97157b
SHA512 (FreeBSD-11.0-RELEASE-amd64.vmdk.xz) = 4900824f1035d5ea1c9fe4c893f701505ad29cb7d8bae4122112835e6901414f9d4b99bce8b25871271a462608b1cdebcf2422181b5b6ffe9cfa32757af3d64f
SHA256 (FreeBSD-11.0-RELEASE-amd64.qcow2.xz) = ecfda452ef0b9387c6934a9e9d7d6a2014ae42464a47cd028f24b4b8377f3cd0
SHA256 (FreeBSD-11.0-RELEASE-amd64.raw.xz) = f9f7fcac1acfe210979a72e0642a70fcf9c9381cc1884e966eac8381c724158c
SHA256 (FreeBSD-11.0-RELEASE-amd64.vhd.xz) = b483d44e9f49bd4eb00d10df500fa14c6fe794c78d7f9bd3377615f28f16394a
SHA256 (FreeBSD-11.0-RELEASE-amd64.vmdk.xz) = 478240fed81dd9dffc3f46bed30c44f16d8fb7bcb078e13c64750811448bae41
i386 (x86):
SHA512 (FreeBSD-11.0-RELEASE-i386.qcow2.xz) = d0e4965b192f0a5e3c1212965d393979eb4b42cd17322f2b959b76efb8ffafffc45523c08c23f94d6d15cd7963f310660e03a9fed946b263f40650ffa9fd4c1f
SHA512 (FreeBSD-11.0-RELEASE-i386.raw.xz) = a57e924500d704c3361a590d0f4b4126e099aab87064ad36dc09b5d4d9e887770f090e22e67bb3b8e9efd79ba9de732d15a318b0021b884596bfc87f46f43b80
SHA512 (FreeBSD-11.0-RELEASE-i386.vhd.xz) = 8bc1e2c25798d7804576c4626947e2c17459ac3cec8731918d45ba42d15f10c9de79d70344ea37937e6af870c801f73a9b173cea1dea3899ae6209b1c769b17e
SHA512 (FreeBSD-11.0-RELEASE-i386.vmdk.xz) = da6dc9310ae8b9d642954f4ad33dfb14a94b4ef8ffd8c56c87a95e8537588e3cea8ba2b74a965017400359945a7079d2c0678306202ea4f2a9eac50ae08f8d3f
SHA256 (FreeBSD-11.0-RELEASE-i386.qcow2.xz) = 3ec41e0797966779861685c7a259dd8ea6392e800909640c90281bdbcf7ec39f
SHA256 (FreeBSD-11.0-RELEASE-i386.raw.xz) = 39c60a0b7b9d18f556c177140d482b88a71457d998c93d3e37675f7f429df5ca
SHA256 (FreeBSD-11.0-RELEASE-i386.vhd.xz) = 2eadf53a9c4f31dd3bf93b3a99f3239ab449e6cb7677797c33c9d680a8c1cde1
SHA256 (FreeBSD-11.0-RELEASE-i386.vmdk.xz) = df76a4d8611a20b0cb15e8557e07206d756b6ce8d55bcfe22b0bc120400a13dc
aarch64 (arm64):
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64.qcow2.xz) = c9d62e5ae6076486eb338a62551d99a9b890c0baf1b11826499806bdf6230dcf7ef1c19c2925e3713cb54aa754aa7b6d75a52e99afde5633ea6da1f01e3aa82d
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64.raw.xz) = 34ec015afd1f879b9b92e6ed9537976b1fd1685f71cf4d06c934917e7e21ad6ade57674c2221babffcd5cb63c128a8f7bc8da762f354597f2d090c9b6bbbea42
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64.vhd.xz) = 93a40e63213cab8126d5d43ce3b42baa33bfbe9a3210c39cc1c8dc9b05c1e52e6d738b1bbfd054b1c77460ef25327ca078593215e44d93c7f21fb14930c32fe9
SHA512 (FreeBSD-11.0-RELEASE-arm64-aarch64.vmdk.xz) = 9f1d7ee8362ddb86a8b600648b2e0c5435c8aacb430fe5c1c141dd197004331b4a7a2285c52e994fa6dc0387a1db4606645b874e6b5bf0fdd0bb0cab49f0fde8
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64.qcow2.xz) = 23d971eca444e99471282b73f1b8964429a666e34368669c059af0ec27f9a64a
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64.raw.xz) = 40fbc3c4c52cdf4b13d55b83bc2545206675aa8dd6e88d57683222dd10f69143
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64.vhd.xz) = 4bd46a52159c088595ad113a89ee273f3567946568dcbbfd31d420bf7995329b
SHA256 (FreeBSD-11.0-RELEASE-arm64-aarch64.vmdk.xz) = 916e8ac1a4ecdc98ccf59e4b5aad8d4473ac5dceeff916581db90f5d442d622c
Love FreeBSD? Support this and future releases with a donation to The
FreeBSD Foundation! https://www.FreeBSDFoundation.org/donate/








 BSD – Magazine
BSD – Magazine FreeBSD Brasil
FreeBSD Brasil Linux-BR
Linux-BR Root BSD
Root BSD